If not redirected, please click here https://www.thesecuritybuddy.com/vulnerabilities/what-is-shellshock-vulnerability/
ShellShock is a security
vulnerability which affects many versions of Unix like Operating
Systems like Linux and results in allowing attackers to gain control
over a system illegitimately.
ShellShock Vulnerability
In Unix, Shell is a command processor
using which commands are executed in the Opetating Systems. Bash
is one such command processor. It is mainly used in text windows, but
many applications also can use it to execute required commands.
Environment Variables are
variables whose values are used to affect the way the running
processes will behave in the computer. For example, an application
process may prefer to store temporary files in a folder. For that
purpose, the running process will check the value of the Environment
Variable called TEMP and store the files there.
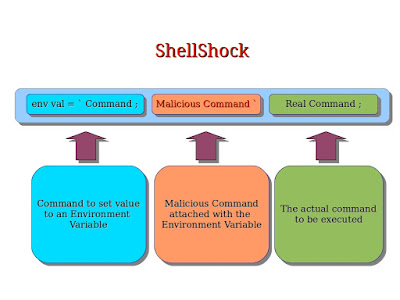
Using ShellShock vulnerability,
an attacker can attach malicious code to some Environment Variable in
Bash and run it to gain control over the system.
Consequences
Many a times Web Servers use
Bash to execute commands. So, the attackers can exploit this
vulnerability to execute malicious commands in a Web Server. And, the
results of that may be as serious as exposing sensitive files like
password files to the attackers or downloading malicious files to the
Web Servers.
Even other devices like Linux based
routers that use CGI for Web Interfaces are vulnerable to tthis
attack. Attackers can exploit ShellShock vulnerability and use CGI to
execute malicious commands in those devices.
IoT (Internet of Things) devices
also may be vulnerable to this attack if they are using Bash.
OpenSSH Servers are also
vulnerable to this attack. Attackers can gain unrestricted shell
access of the server exploiting ShellShock.
Other than that, Computers running
Mac OS X, DHCP Clients, Qmail Server and IBM HMC
restricted shell are also vulnerable to this attack.
Prevention
There are a number of reports of
exploitation of this vulnerability by the attackers. But, the good
news is that a number of Operating Systems vendors who are affected
by this vulnerability have already issued patches. Website owners and
business owners should apply those latest security patches to their
Operating Systems to avoid ShellShock Attack.
However, users are also advised to
apply recent security patches for their web enabled devices like
routers, IoT devices and embedded devices etc to prevent this attack.
So, beware of various security
vulnerabilities, so that you can protect yourself in a better way.
And, stay safe, stay secured.
No comments:
Post a Comment