If not redirected, please click here https://www.thesecuritybuddy.com/dos-ddos-prevention/iot-botnet-and-ddos-attacks/
Towards the end of October, a huge cyber attack took down the internet in many parts of the world. It was caused by a DDoS attack made by a IoT botnet. But, what is a IoT botnet basically? And, how can it make such a huge DDoS attack? In this article we would take a deeper look into that.
Towards the end of October, a huge cyber attack took down the internet in many parts of the world. It was caused by a DDoS attack made by a IoT botnet. But, what is a IoT botnet basically? And, how can it make such a huge DDoS attack? In this article we would take a deeper look into that.
What is IoT Botnet ?
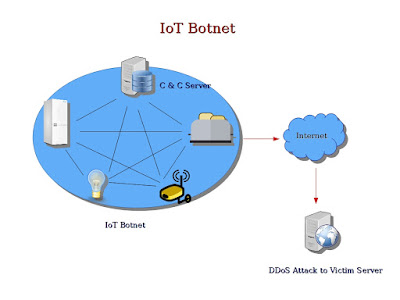
A botnet is basically a group of internet connected devices which are
controlled by the attackers for illicit purposes like stealing
sensitive information of users, sending spams, generating false
traffic to malicious websites using Click Fraud or making a DDoS
attack to suspend a service or an entire network completely for an
indefinite time.
IoT is made up of not only dedicated computers, but also healthcare
devices like cardiac implant monitors, household and industrial
appliances, automobiles, mechanical sensors and other smart
appliances. When attackers hack IoT devices to create a botnet and
exploit that for malicious purposes like making a DDoS attack, it is
called a IoT botnet.
To create a IoT botnet, attackers usually infect a group of IoT
devices with malware and gains unauthorized access of the devices.
These hacked devices are called zombies. The attackers then create a
network of these hacked zombie devices and control them to exploit
their computation power for illicit purposes like making a DDoS
attack.
What is a DDoS Attack ?
A
DoS or
Denial of Service Attack is
an attack which is perpetrated for the purpose of making a target
machine or network resource unavailable for its intended users. This
attack is usually made to temporarily or indefinitely suspend a
service of a host connected to internet.
DDoS
Attack or Distributed Denial of Service Attack is
a DoS
attack in which the attack comes from multiple sources having
different IP addresses. Basically, a DDoS attack is a DoS attack in
which the attack is perpetrated using several source IP addresses.
Using IP address spoofing, the attackers normally hide their own IP
addresses, making it extremely hard to catch the attackers.
How can a IoT Botnet be used to make a DDoS Attack ?
A
very good example of such IoT botnet is the botnet which affected
websites from Twitter to Reddit in October 21, 2016. Attackers used
malware named “Mirai” to infect IoT devices and created a huge
botnet out of them. The IoT botnet was then used to launch a DDoS
attack on the servers of DYN, which provides a dynamic DNS service
named DynDNS.
The
attackers first scanned for IoT systems with default usernames and
passwords or IoT systems configured with weak credentials. Such IoT
systems were then infected with Mirai malware to make them part of a
IoT botnet. Mirai could break into a wide range of IoT devices from
CCTV cameras to DVRs to other smart home appliances to turn them into
bots. Attackers created nearly half a million Mirai powered bots in
such way. The IoT botnet then exploited the computation power of
those hacked IoT devices to make a huge number of requests to servers
of DYN, which provides service for dynamic DNS.
When
a device wants to access any website or server, it makes a DNS query
to resolve the IP address of the server. The DNS servers provide the
IP address to the client device, using which the device can connect
to the required server. But nowadays, usually Dynamic Host
Configuration Protocol or DHCP is used to configure IP addresses of
servers, which keep changing over time. And to manage that, so that
DNS servers can always point to the correct IP addresses, Dynamic DNS
is used.
DYN
provides Dynamic DNS services to websites like Amazon, Spotify and
Twitter. As a result, when the IoT botnet attacked the servers of
DYN, those websites went down, creating a huge internet outage. In
fact, the IoT botnet was so huge that it started making tens of
millions of requests at the same time to the servers of DYN to
suspend its services.
There
are a number of other IoT botnets also, which hack the IoT systems
and exploit them for malicious purposes. Bashlight and Aidra are two
of them.
How to secure IoT Devices ?
The
good thing is, we can always take a couple of simple steps to secure
the IoT devices.
-
Always remember to change the default passwords of IoT systems while configuring it. When attackers try to hack a IoT device, the first thing they do is to try a list of easily available default usernames and passwords of devices to gain access.
-
Do not keep weak passwords. You can find a simple suggestion on how to create a strong password and remember it efficiently at the same time here: How to create a Strong Password
-
Enable 2 Factor Authentication wherever possible.
-
Update firmware of IoT devices regularly. More updated a firmware is, lesser are its security vulnerabilities.
-
Enable Firewalls and IDPS wherever possible.
-
Please make sure only the necessary ports of the IoT devices are open and exposed outside.
-
Please make sure network ports or services are not exposed to the internet via UPnP.
-
Use accepted encryption standards and proprietary encryption protocols to encrypt data in IoT systems.
-
Please ensure physical security of IoT devices. Please make sure data storage medium cannot be easily removed and only the external ports that are necessary are used.
Read More
How to prevent DoS and DDoS attacks ?
What is Deep Packet Inspection ?
How to secure IoT devices ?
What is Next Generation Firewall ?
How can Fog Computing improve security and privacy of IoT ?
How to create a strong password that can be remembered easily ?
What is an Intrusion Detection System and how does it work ?
What is Honeypot ?
Infographic : Do's and Don'ts of Passwords
What is Blockchain and how can it be used in IoT ?
informative content
ReplyDeleteThanks Sanjana.
ReplyDelete