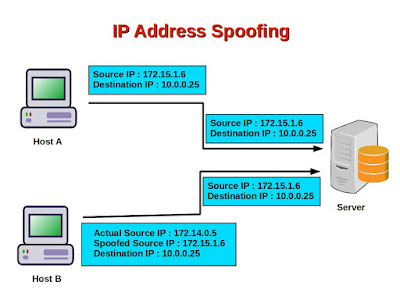
In one of my last articles, I
explained, what is
IP Address Spoofing. (
What is IP Address Spoofing Attack ? IP
Address Spoofing attack )
In fact, in almost all cyber
attacks, the attacker spoofs his IP address so that it becomes very
difficult to catch the attacker.
But how do the attackers do that? How
can they change IP address of outgoing IP packets?
Well, in this
article, I am going to show you that. And again, I will show the
methods for Ubuntu, because I use Ubuntu for experiments.
So,
let's start.
I think, by now we all know about how to set Linux firewalls using
iptables (
How to configure Linux Firewalls using iptables ? how
to set Linux firewalls using iptables.)
The
firewalls (
What is firewall ? firewalls) mainly, inspect all incoming and outgoing IP packets and accept or
reject them based on some predefined rules.
In fact, using
Linux iptables, we can easily change source IP of our
outgoing packets. Iptables give us this option because it is very
useful for network testing and diagnostics and security penetration
testing.
We need to execute a single command, with root
permissions, to do that.
#
sudo
iptables -t nat -A POSTROUTING -p icmp -j SNAT --to-source
192.168.1.121
This rule says, for packets using ICMP
protocol, the source IP address will be changed to 192.168.1.121.
This rule will be applied to outgoing packets, after they have completed
the routing procedures in the machine and is about to be sent
outside.
Now, before executing the command, I
had seen all the IP addresses present in my local network using the
command 'arp-scan'.
# sudo arp-scan -interface=eth1
--localnet
Interface: eth1, datalink type: EN10MB
(Ethernet)
Starting arp-scan 1.8.1 with 256 hosts
(http://www.nta-monitor.com/tools/arp-scan/)
192.168.1.1
48:8f:b3:63:20:a5 (Unknown)
192.168.1.120
07:63:97:c8:f1:c5 (Unknown)
192.168.1.133
00:1f:3a:bc:7b:58 Pr_Bc
192.168.1.138
cf:4b:63:7f:04:84 (Unknown)
192.168.1.117
cd:c5:eb:68:22:4b (Unknown)
5 packets received by filter, 0 packets
dropped by kernel
Ending arp-scan 1.8.1: 256 hosts
scanned in 1.289 seconds (198.60 hosts/sec). 5 responded
So, here the IP address 192.168.1.121
does not exist.
Now, I open the machine and type:
#
ping 192.168.1.116
Can you guess what should be the
outcome of this ping?
No reply. Because this IP address does
not exist at all. So, the destination machine, with IP address
192.168.1.116 will receive the ping message and make an ARP query to
find out what is the hardware MAC address of this IP. But, the
machine will not get any reply and won't be able to respond to the
ping's. As a result, the source machine, with IP address
192.168.1.133, will get no reply at all.
Let's do
something different now. Let's delete this iptables rule and execute
some different commands.
# sudo
iptables -t nat -D POSTROUTING -p icmp -j SNAT --to-source
192.168.1.121
#
sudo iptables -t nat -A POSTROUTING -p icmp -j SNAT --to-source
192.168.1.138So,
we have deleted the previous rule from the machine with IP address
192.168.1.133 and added a new rule, so that, the source IP address of
all outgoing ICMP packets are now 192.168.1.138.
Now, I would execute the ping command in the machine 192.168.1.133, where I have
changed the iptables rules.
# ping 192.168.1.116
Will
we get any reply now?
Well, no. Because we have pinged the
machine 192.168.1.116 with a forged IP address. But the machine does
not know that the source IP address of the packets are forged. So, it
will send replies to 192.168.1.138.
In fact, if I do the same
steps from multiple machines and change the source IP address of all
outgoing ICMP packets to 192.168.1.138 and ping different machines,
all the machines will send replies to 192.168.1.138 and will eat up
all its bandwidth, causing a Denial of Service or DoS attack for the
machine 192.168.1.138. Does it remind us of Ping Flood ? (What is Ping Flood ? Ping
Flood)
Now,
the most vital question will come to our mind,
Is it possible
to know from the machine 192.168.1.116 that the ping messages it
received were spoofed ones?
Let's
try.
We would open Wireshark from a terminal.
# sudo
wireshark
A window will appear similar to the below
one.
Click on the interface you want to listen. In my case, it
is eth1. And then, click on any ICMP message coming from
192.168.1.138.
If
we click on Ethernet II, we see, source MAC address is
00:1f:3a:bc:7b:58.
But from the 'arp-scan' output, we saw, the
machine with IP address 192.168.1.133 has MAC address
cf:4b:63:7f:04:84, which is an anomaly.
You can confirm the
same with tcpdump also.
So, if the attacker forges the source
IP address of his packets to contain the IP address of some machine
within the victim's local network, then the victim can verify
and find that out.
But if it is not within the local network, then it
is very difficult to find that out. Configuring a strong firewalls is
always the best option.
So,
in this article, I wanted to show you how IP
address spoofing can be done easily. If you think it has helped you anywhere in thinking about
safeguarding your system, I think my job is done.
So, stay
safe, stay protected!