If not redirected, please click here https://www.thesecuritybuddy.com/vulnerabilities/what-is-heap-spraying/
Heap Spraying is a technique
using which an attacker can write certain sequence of bytes at a
predetermined memory location of a process and then exploit that to
facilitate execution of arbitrary malicious code.
Let's try to understand what it
actually is.
What is Heap
A process in execution uses different
sections of memory for different purposes.
To name a few :
Text Section : Text Section
is used to store static code of the program. It is usually marked as
read-only and cannot be modified by the program.
Data Section : Data Section
is used to store static and global variables.
Stack Section : Usually every
function uses some local variables. They are in use as long as the
process executes that particular function and after that they are not
needed anymore. A process uses Stack Section to store those
local variables. Memory is allocated when the function is called and
it is freed upon returning from the function.
Heap Section : Many a times it
is not possible for a process to know in advance how much memory it
would need for a certain variable. A dynamic array or a linked list
may be a good example of that. For that purpose, the process
dynamically allocates memory for that variable at run time. For
storing these dynamically allocated data, a process uses Heap
Section.
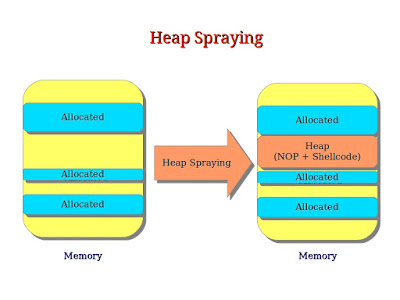
In Heap Spraying, the attacker writes
series of bytes in Heap Section of a process and later exploit that
for malicious purposes, usually in a separate attack.
How is Heap Spraying perpetrated
In Heap Spraying, the attackers
exploit the fact that heap is usually deterministic. It often starts
at a predetermined location in memory and located in consecutive
manner.
So, the attackers first use some
mechanism to put their shellcode to some predictable location in the
heap and then, trigger a bug to make the EIP instruction pointer to
directly point to the location.
A browser is an easy mechanism to do
this. The attackers can use scripting support to spray the heap and
then trigger the bug.
The attackers can even use other
mechanisms like JavaScript or Actionscript in Adobe Reader to put the
shellcode in predetermined location in the heap.
So, to summarize, in Heap Spraying the
attackers first take scripting support to put their shellcode in the
heap section of the process. After that, they trigger a bug and make
the instruction pointer point to the predetermined location.
Detection and Prevention
There are a couple of ways of detection
and prevention of Heap Spraying :
- The Nozzle Project of Microsoft Research aims to detect and prevent Heap Spraying.
- BuBBle is another countermeasure which can be used in detecting and prevention Heap Spraying. BuBBle is basically a JavaScript Engine level countermeasure for Heap Spraying.
So, beware of various security
vulnerabilities so that you can protect your systems in a better way.
And, stay safe, stay protected.
No comments:
Post a Comment